某音27.8版本Hook,X-Medusa,X-Helios,X-Argus,X-Ladon,X-Gorgon,X-Khronos
本文章仅供学习研究,读者请勿用作非法用途,如若侵权,请联系第一时间进行删除。
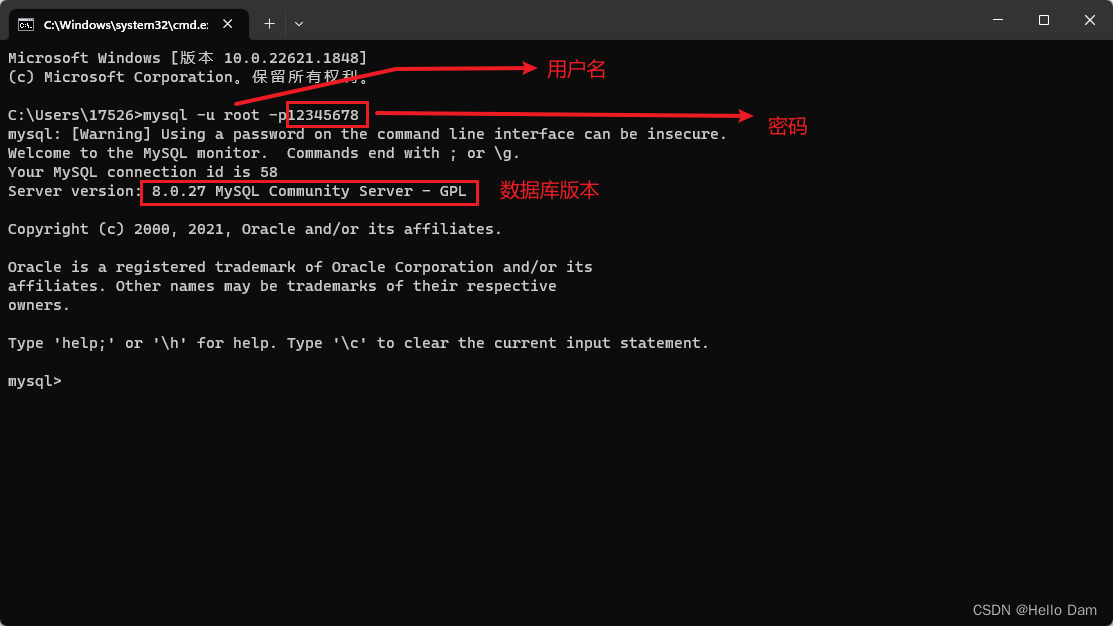
两个关键的地方的路径
(图片来源网络,侵删)
com.bytedance.mobsec.metasec.ml.MSManager
com.bytedance.frameworks.baselib.network.http.NetworkParams
三个关键的函数
setDeviceID
setInstallID
tryAddSecurityFactor
Hook这三个函数即可返回得到值,以下是Hook的Js代码
var six = function (did, iid, str, map) {
var result = "";
var Map = Java.use("java.util.TreeMap").$new();
var HashMap = Java.use("java.util.HashMap").$new();
var strArray = new Array();
strArray = map.split(",");
for (var i = 0; i
python使用frida rpc调用即可,fastapi暴露接口,调用例子如下
@app.post('/six')
def encrypt_six(did: str = Form(...), iid: str = Form(...), url: str = Form(...), header: str = Form(...)):
url = urllib.parse.unquote(url)
header = urllib.parse.unquote(header)
data = script5554.exports.encrypt(did, iid, url, header)
return data
def sign(did, iid, url, header):
payload = f'did={did}&iid={iid}&url={urllib.parse.quote(url)}&header={urllib.parse.quote(header)}'
response = httpx.post('http://127.0.0.1:9002/six', headers={'Content-Type': 'application/x-www-form-urlencoded'}, data=payload)
return response.json()
promotion_id = '123456789'
ticket = int(round(time.time() * 1000))
ts = int(time.time())
url = f'https://ecom5-normal-lq.ecombdapi.com/aweme/v2/shop/promotion/pack/?iid=25974xxxxxxxxxx'
headers = {
'Host': 'ecom5-normal-lq.ecombdapi.com',
'Cookie': 'Cookie',
'x-tt-dt': '',
'x-bd-kmsv': '1',
'sdk-version': '2',
'X-Tt-Token': '',
'passport-sdk-version': '203157',
'x-vc-bdturing-sdk-version': '3.7.0.cn',
'Content-Type': 'application/x-www-form-urlencoded; charset=UTF-8',
'X-SS-STUB': '',
'x-tt-request-tag': 's=0;p=0',
'X-SS-DP': '1128',
'x-tt-trace-id': '1',
'User-Agent': '',
}
header = (f'Content-Type=[application/x-www-form-urlencoded; charset=UTF-8],'
f'X-SS-STUB=[{hashlib.md5(data.encode()).hexdigest().upper()}],'
f'User-Agent=[{headers["User-Agent"]}]')
#print(header)
print(url)
six = sign('', '', url, header)
print(six)
如需技术交流可以T,G搜索 @LuxoPus5896
文章版权声明:除非注明,否则均为主机测评原创文章,转载或复制请以超链接形式并注明出处。



.png)